Introduction
In this post, we are going to see how the ATECC608A microchip works. It is a microprocessor used for network security and authentication. Therefore, it is very important to provide security to all those devices which have not got it from their stock versions.

Related links
Computer Networking: A top Down Approach, Jim Kurose, Keith Ross (bibliography of the images and it is interesting for related information)
Microchip
It has all the mechanisms to provide a full range of security such as confidentiality, data integrity, and authentication to MCU or MPUs systems running encryption/decryption algorithms. It employs ultra-secure hardware-based cryptographic key storage and cryptographic countermeasures which eliminate potential backdoors linked to software weaknesses.
The device is agnostic of any microprocessor or microcontroller, and compatible with Microchip AVR/ARM MCUs or MPUs. It offers extremely low-power consumption, requires only a single GPIO over a wide voltage range, and has a tiny form factor, making it ideal for a variety of applications that require long battery life and flexible form factors.
Key features
Cryptographic co-processor with secure hardware-based key storage.
Protected storage for up to 16 Keys, certificates or data.
Hardware support for an asymmetric sign, verify key agreement - ECDSA.
Hardware support for symmetric algorithms.
Support for networking key management.
Secure boot support.
Etc.
Security systems
Elliptic Curve Diffie Hellman (ECDH)
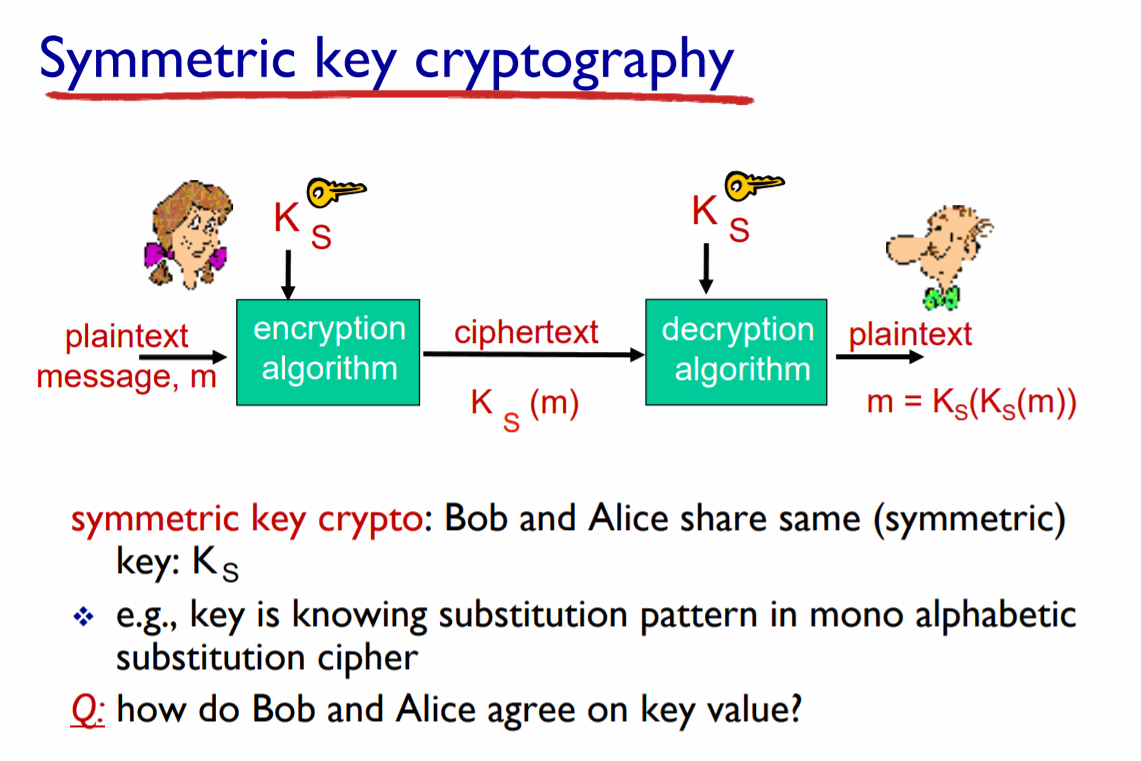
It is an ultra-secure protocol that provides a key agreement for encryption/decryption. It is based on a completely anonymous key establishment which allows the two parts (each one has a pair of private-public elliptic curve keys) to establish a shared secret in an insecure channel. This shared secret can be used directly as a key or to derive another key. The key, or private key, can be used to encrypt successive communications using the symmetric key. The elliptic curve part is based on that, both parts have a pair of specialized cryptography keys (one public and one private, as we saw previously). Private-Public key encryption is a method that we could go into much more detail about, as well as the hash function, which is usually applied to the secret in order to eliminate weak bits due to the Diffie-Hellman exchange.
In this image, you can see an example of symmetric key cryptography, but you have to take into account that this is only a part, in the absence of the Private-Public key and the hash parts if they are needed. (It is not exactly the ECDH mechanism, it is only for explanation purposes).
Elliptic Curve Digital Signature Algorithm (ECDSA)
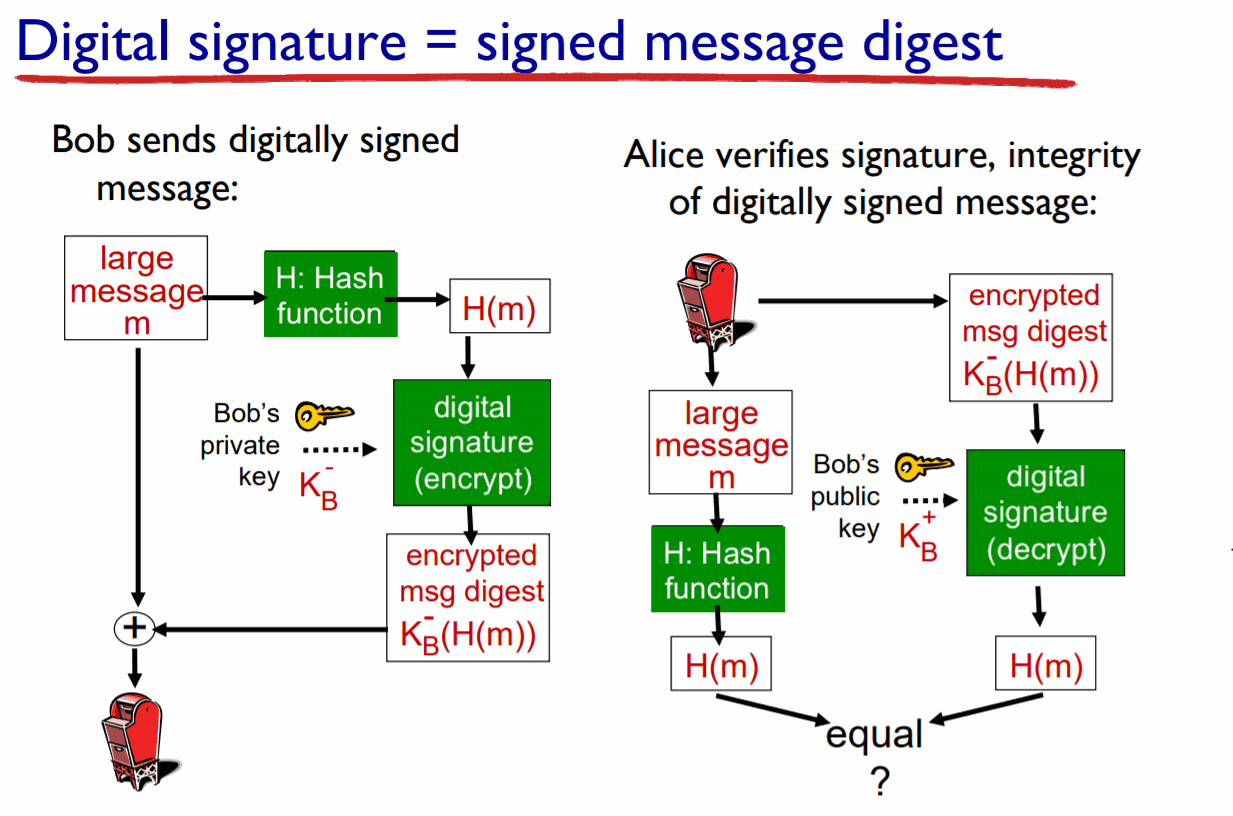
It is a sign-verify authentication for the Internet Of Things market. The main advantage of this system is that it requires smaller numbers to provide the same security level as DSA or RSA. The whole process consists of generating the keys (Private-Public previous key system), signing verification (using mathematical algorithms).
.
Here we can see another example and, as in the previous one, the two parts are represented by Bob and Alice. Bob sends a digitally signed message; on the one hand, the large message is sent in the original format and, on the other hand, a hash is applied to the message to ensure its integrity, it is digital signed (encrypted) with Bob's private key and sent too.
After that, Alice verifies the signature and the integrity of the digitally signed message; on the one hand, she applies a hash function to the message and, on the other hand, she decrypts the encrypted message with Bob's public key. She has two encrypted messages with the same hash function and she compares both to verify Bob's authentication. (It is not exactly the ECDSA mechanism, it is only for explanation purposes).
Network security with ATECC608A and industrial automation