Introduction
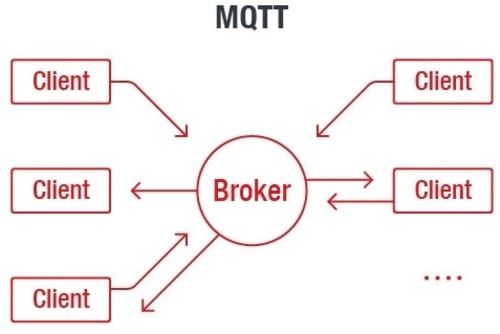
There is a worldwide concern about the security of our personal data, so in this post, we are going to mention the different security methods that can transfer data over the broker to get to the client in a safe way.
These security methods are initiated by the broker and it is up to the client to comply with these mechanisms. It is also important to check the capabilities of your MQTT clients as well as your broker.
MQTT basic Security
Security in MQTT is usually divided into several layers to prevent different kinds of attacks. Where the MQTT wants to get is to provide a light and easy to use communication protocol for the Internet of Things (IoT).
The protocol itself specifies only a few security mechanisms. MQTT implementations commonly use other state of the art security standards like SSL/TLS for transport security, TCP/IP stack, x509 Client Certificate Authentication and others.
The division of the security levels in MQTT would be the following one:
Network level: to provide a reliable connection we need to use a physically secure network or VPN for all the communication between clients and brokers. This solution can work with gateway applications where the gateway connects to devices and also to the VPN.
Transport level: SSL/TLS is commonly used for transport encryption when confidentiality is required. Data cannot be read during transmission due to this secure method and provides client-certificate authentication to verify the identity of both sides.
Application level: the MQTT protocol provides a client id, client identifier and username/password credentials to authenticate devices on the application level. These properties are provided by the protocol itself. What the devices are allowed to do is defined by the specific broker implementation. At the application level, it is also possible to use payload encryption to secure the transmitted information without the need for transport encryption.
After talking about how to secure MQTT on a protocol level and implementing security on the application level, we are going to talk about the secure deployment of an MQTT system. We’ll go over the different layers of security and how to strengthen the prevention of attacks.
The different layers of security to focus on in this case are:
The infrastructure: MQTT brokers typically run on network infrastructure. It is important to understand the network topology of the target system, a part of locking out attackers as soon as possible to prevent damage and downtimes of downstream systems. All the connections to an MQTT broker should go through, at least, one firewall.
The operating system: MQTT brokers are installed in servers running several operating systems and many attacks are focused on the security holes of the operating system or software.
The MQTT broker: the main advantages of the MQTT broker are the following ones: it eliminates insecure and vulnerable clients' connections, it can easily scale from a single device to thousands, it tracks and manages all the connection states of the clients and it can work with lower network tension without compromising the security.
Conclusion
When talking about the MQTT's system security, we can say that it can be a challenge. Security needs to be considered at a high number of levels, so it is essential to know the infrastructure of the network you are working with, apart from your servers. They both need to be configured conscientiously and suitably.
MQTT Security Fundamentals in industrial automation